FCS-CTF
Anythink 5.0 Challenge
Welcome to Anythink 5.0 Challenge. We are grateful that you are attempting our challenge.
Note: For any help that you need, you can pm either one of us below via telegram.
Note: Each of us are tagged to an operating system
Windows:
Leon
Sean Gunawan
Update: All GUI has become CLI. For the email section please ignore the hint.
Prerequisites
To complete this lab, you would need to do the following on your system to be able to complete the challenge.
- Generate a pair of rsa private and public keys 2048 bits will be the correct size. Send us your key through a single member, ideally the group leader. Don’t flood us thanks!
- You would also need python3 minimum python 3.8 to solve our challenge.
- For windows users, please ensure that Putty is working (recommended to ssh easily). Note: Ports 22, 3389 are open, make use of them wisely.
Key generation
For POSIX compliant systems, you can use a terminal of your choice to ssh in.
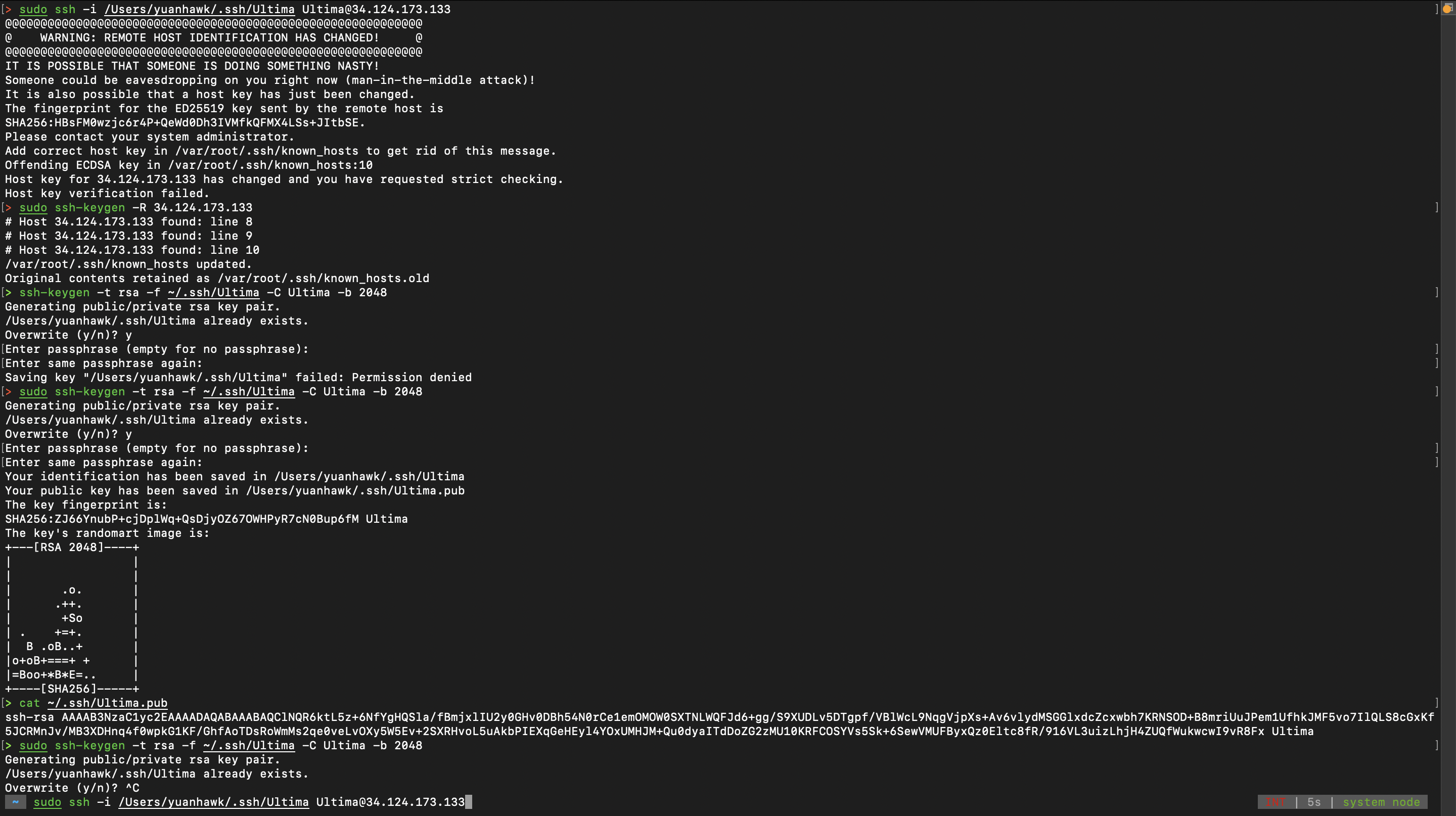
Here is a list of suggested commands to get yourselves in! Disclaimer: This is part of the setup process, and it is not in our interest to make you suffer or read documentations for this portion of key generation.
sudo ssh-keygen -t rsa -f ~/.ssh/Ultima -C Ultima -b 2048
The password is sutd1234
cat ~/.ssh/Ultima.pub
send your public key only!!! else we can hack hack :D
sudo ssh -i ~/.ssh/Ultima Ultima@<ip address>
For Windows, Utilize PuTTYgen to generate a public key and private key associated with the Ultima account, send the public key to one of the Challenge Masters to gain access to the SSH.
It is very important to use Ultima as the account
Important: please pass us your public key only!!!! It should be in the following format:
COPY AND PASTE THIS ENTIRELY and send it to one of us via pm
ssh-rsa <whatever the key is here> Ultima
Troubleshoot
If you have something of this sort, do consider attempting this, before resending the rsa pub key!
Small Guide
To make the challenge friendly to solve, we will let you know what you need to use to solve. Just follow our guide carefully to be able to solve our challenge.
To start you off, a very big hint would be to use what you have learnt from the labs as well as Computer Systems Engineering module in the previous term to be able to solve our challenges. If you understand the labs or what was taught in class, you should be able to solve the challenges.
Background
We have a very lazy system administrator lying around and the system has files lurking everywhere such that military secrets of the navy can be compromised. Of course certain data that should not be read can be read. A food for thought would be that under the BLP model, what security rules are violated and and what level can non-super users read and write the data accordingly. A user Ultima holds the access to the personal account code and which can lead to the access of the admin account. Getting into the admin means that access to the navy can be leaked within 2 hours.
IMPORTANT: We are all counting on you to prevent the leak of secrets.
Starting off
- SSH into the system with the following PM Li Yuan for the IP address for each group, we have setup the respective ip address please stick to your own ip addresses else it’ll be unfair to everyone.
If you know the password to the admin account, the username is admin and the password is for you to guess or do it via personal account which has the username Ultima in this case.
Personal Account: Ultima
Challenge 1
Hint: Find an image to decrypt the underlying password for an email, send in your best guesser and hope for the best
Hint: The keyspace is only the alphabet, space, and period, the target string is in lower-case Here’s the slides for what you can solve to find the underlying password: https://docs.google.com/presentation/d/1ZTpdh4HeGxT5N2iAi1kty68xf9_eOYOiAgwLOaHoVtY/edit?usp=sharing
Challenge 2
Objective: Find the password for the admin in an encrypted email
Note that the email has salt. Think of some tools to crack!
Hint: To decrypt the email, ensure you get a tar file after you decrypt this folder.
The extension in the $HOME folder should tell you what the folder is encrypted in.
The mode to decrypt is CBC mode. You need not specify the salt.
VERY BIG HINT: In one of the files, please please look for the password to the admin! It shouldn’t take you longer than 10 minutes.
If you have any issues with the encrypted folder, please pm Melody.
You can use tools to decrypt the file.
It would be best for you to make a copy of the encrypted folder before attempting to decrypt it.
Alternative path to admin
If the above challenges aren’t your cup of tea, there is another way in - try looking in some user files…
(Yes you can avoid challenges 1 and 2 and do this instead)
Admin
Challenge 3
Hint: Run the challenge.sh script, but its self-destructible, you can find ways to stop it… Remember the admin is lazy, so with the password hint, and some guesses, you should be able to guess it.
Path dir
Updated password text (we have reduced to abt 50 passwords)
, find in ~
Suggested approach: write a bash script to test dictionary of admin passwords.
Tools to be used: aescrypt, find in ~/Downloads
Tools to be ignored: password-permutor
Passwords can be found in the $HOME directory
Challenge 4
Update:
~/Pictures/.local/.hint
Tools to be used: outguess, find the tool in ~/Downloads
Things that you might need to think of
- RSA
- Common Image Analysis techniques.
- Linux file system. You can scroll around to find what you need to use to piece together for each challenge. Solving each challenge will enable you to solve the other challenges.
- Crypto techniques. Don’t worry they are pretty weak such that we have not enabled so many paddings.
- Passwords that you may need are of the common passwords that can be cracked.
- Command Line Tools